# DigiD
TIP
Read more about DigiD in the Knowledgebase.
# Getting started
You can add DigiD as an authentication provider from the federation dashboard in the Identity Broker.
The establishment of DigiD consists of:
- Your technical integration with Signicat. Please see here to get started.
- The ordering process of PKIoverheid certificates (opens new window) (for both pre-prod and production) from one of the approved PKIoverheid issuers. (Read more about getting certificates in the Identity Broker here.)
- The registration of your certificates and metadata at Logius. Signicat will guide you in this process and provide you with the correct metadata.
- The approval of your implementation by Logius, both for pre-prod and prod. We will share the details of this process with you via email.
- Both your pre-prod and production connection need to be approved by Logius. Logius will use this checklist (opens new window) (opens new window) to check your implementation.
# Certificate information
The Signicat Identity Broker must be configured with two PKIO certificates, one for pre-production and one for production. These certificates will be used to cryptographically sign the messages between the Signicat Identity Broker and the DigiD network.
TIP
Check out the page Certificates in Identity Broker for a clear outline of the steps involved.
# DigiD settings
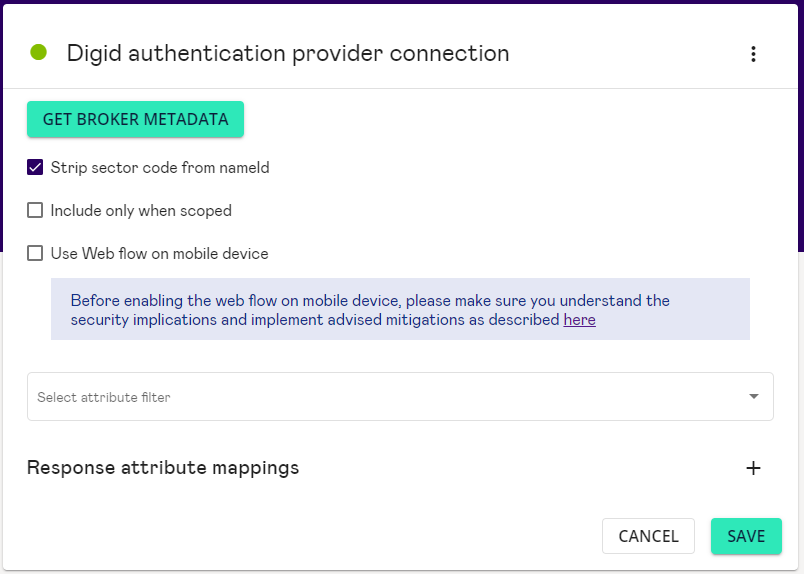
- Strip sector code from nameID checkbox: Logius sends a prefix with the citizen service number (BSN). Some service providers can't handle that, so with this option you can strip away the sector code/prefix.
- Include only when scoped checkbox: The broker provides scoped IdP functionality.
- Use Web flow on mobile device checkbox: If you are configuring the WEB flow for your connection, you may still want to use it from mobile devices. If you are using the DigiD app, the redirect back to the broker will in some situations open in the mobile device's native browser. In such cases, we need to perform an operation called "session restoration". This comes with certain security issues. We have taken a number of mitigations on our side in order to reduce the risks of such threats. However, there are still risks that can not be mitigated on our side. If you want to use this option, you have to accept these risks. For further information please contact our Technical Support.
In order to fully mitigate the residual risk, we advise our service provider customers to on their side implement the following: You should only accept a response from the Signicat Identity Broker if you are able to match that response to a request that you have sent earlier. You can achieve this, for instance, by storing the request you have sent in the user session. - Select attribute filter: Attribute filters allow you to filter out certain attributes to make the response more concise for further processing in your software.
- Response attribute mappings: The user can choose to customise the name of the attributes received in the response body. You can provide none or multiple name-to-name mappings.
Connection type
To configure the connection type, such as App2App, browser or both, please contact Technical Support at technicalsupport@signicat.com or by calling + 31 (0)88 012 0210.
TIP
See Broker Features for more information.
Adjust the settings as necessary and Save the connection.
# Broker metadata
Once the connection is saved, press the Get Broker Metadata button. You will get the broker metadata xml file which should be sent to Logius.
# Integration with DigiD through Signicat
There are four levels of authentication strength available in DigiD:
- Basic (Basis) - username and password.
- Middle (Midden) - username, password and an additional SMS with one time verification code.
- Substantial (Substantieel) - authentication with a method which is issued after checking the holder’s identity document.
- High (Hoog) - authentication with a personal certificate on an identity document.
A service provider must choose the required authentication security level for its services. This will set the minimum level for the service. The Standardisation Forum can help you determine which assurance level would be suitable for your service in the Level of Assurance Guide (opens new window).
# Points of attention:
- Because Signicat does not use the Single Sign On (Eenmalig inloggen) functionality within DigiD, there is no need to use the sign-out functionality from the DigiD side (Federatief uitloggen). However, DigiD requires that the end-user should be able to sign-out. This function must be implemented by the customer.
IMPORTANT
If you want to make use of DigiD Single Sign On (Eenmalig Inloggen), make sure you have a PKIO certificate that covers the regular broker domain and the client authentication domain.
- The customer is also obliged to manage a local session for the end-user. For this session, a maximum inactivity period of 15 minutes applies. This must be implemented by the customer as well. The customer must be able to recognise replay attacks and be able to mitigate these attacks.
# Available attributes
The main attributes you will receive are the following:
- The confidence level of the authentication. This confidence level will be equal to or greater than the requested level. The optional values are:
| Confidence level | Code |
|---|---|
| Basis | urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport |
| Midden | urn:oasis:names:tc:SAML:2.0:ac:classes:MobileTwoFactorContract |
| Substantieel | urn:oasis:names:tc:SAML:2.0:ac:classes:Smartcard |
| Hoog | urn:oasis:names:tc:SAML:2.0:ac:classes:SmartcardPKI |
- A combination of sector code with personal number. The sector code can have the 2 values below, and describes the type of the personal number.
| Sector code | Type of personal number |
|---|---|
| S00000001 | Social security number, used by (for example) Social Insurance Bank (SVB) for Dutch nationals who emigrated before the BSN was introduced. |
| S00000000 | BSN |
Example: s00000000:900117448
The service provider must implement a correct interpretation of the sector code. This means: checking whether the sector code as returned complies with the expected sector code and handle it appropriately; if an unexpected sector code is returned, the authentication must be cancelled.
If you have also enabled other authentication methods than just DigiD you can use the NameQualifier attribute in SAML responses to your Service to detect in your application that DigiD was used to log in for this request:
<saml:Subject>
<saml:NameID
Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified"
NameQualifier="https://was-preprod1.digid.nl/saml/idp/metadata">
sector number:bsn
</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData
InResponseTo="..." NotOnOrAfter="..." Recipient=".../>
</saml:SubjectConfirmation>
</saml:Subject>
# Using DigiD in the Signicat Enterprise Sign API
Signicat supports electronic signing with DigiD. You can use this method through our Enterprise Sign API.
If you would like to DigiD as a signing method, we need to activate the necessary configurations on your account. To do this, contact us at technicalsupport@signicat.com or visit our Contact Support (opens new window) page.
# More information
If you would like to, you can request a free trial (opens new window) of the Signicat Identity Broker.
# Other resources
- DigiD checklist (opens new window) (pdf)
- DigiD website (opens new window)
- Logius website (opens new window)
# Support
In case any of the steps mentioned above are unclear, please contact Technical Support via email or by calling + 31 (0)88 012 0210.
← OwnIdP Communication →