# SAML Attribute Consuming Services
# Introduction
Security Assertion Markup Language (SAML) allows identity providers to pass authorisation credentials to service providers. With this, you can use one set of credentials to log into many different websites. Your service (set up in Service Providers) can consume SAML assertions from the selected identity providers.
SAML allows identity providers to pass authorisation credentials to service providers. With this, you can use one set of credentials to log into many different websites. Your service (set up in service providers) can consume SAML assertions from the selected identity providers.

This section looks at how the "service" in the Service Provider end of the Broker can be configured. In SAML, requested attributes can be conveyed in two ways:
- Via the requested attributes extension in the AuthnRequest (opens new window).
- Via Attribute Consuming Services in the metadata, and (optionally) an AttributeConsumingServiceIndex in the request.
It is good to know that the Signicat Identity Broker supports both methods. The requested attributes extension comes as part of the AuthnRequest and requires no additional configuration beforehand.
In case the SAML Identity Provider of your choice is only supported via Attribute Consuming Services in the metadata, the Attribute Consuming Services need to be configured. Our user interface helps easily define those.
# Configuration
First, click and create a SAML Attribute Consuming Service in the configuration app:
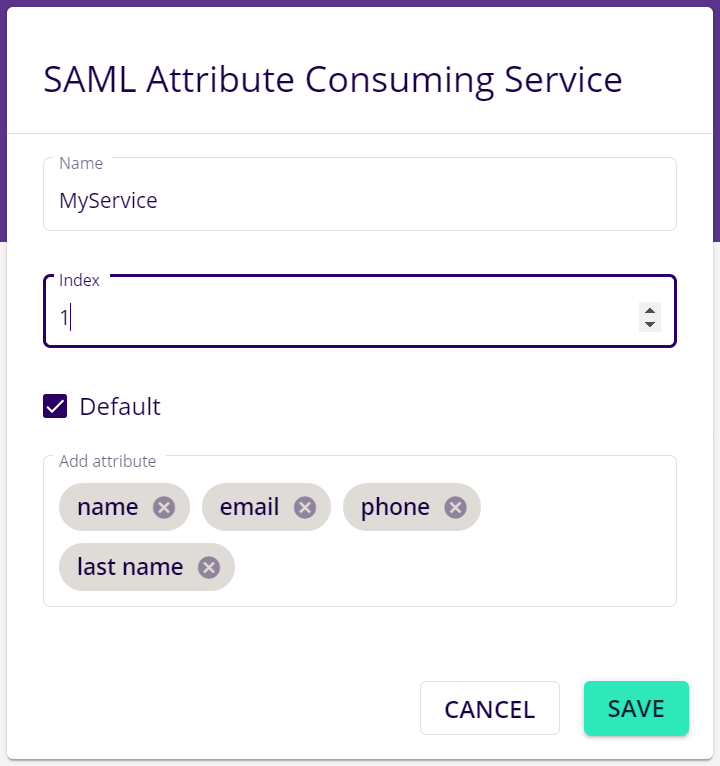
- Name: This can be used to clearly describe for which service you need the specified attributes.
- Index: This will be used to convey to the Identity Provider which attribute consuming service to use, using the AttributeConsumingServiceIndex.
- Default: If selected, this Attribute Consuming Service will be requested by default (in case no AttributeConsumingServiceIndex is sent).
- Attributes: These are the attributes that you require for your service (Check with the SAML Identity Provider of your choice, whether it supports these attributes).
After that is done, the metadata will be updated. To view the broker metadata, go to the configured SAML Identity Provider (in Authentication Providers) or configure a SAML Identity Provider.
In the SAML Identity Provider configuration screen, click on the Get the broker metadata button.
In the metadata the AttributeConsumingService has been added:

Send the new metadata file to the SAML Identity Provider.