Qualified Timestamps (QTSA)
Introduction
Signicat offers Qualified Timestamping Authority (QTSA) services which can be used for issuing a qualified timestamp and binding that timestamp to a data object.
The most common use cases are the timestamping of signed documents and the timestamping of documents that are stored in an archive.
Key security features
Qualified Timestamping Authority services can only be operated by a Qualified Trust Service Provider (QTSP) and require annual audits by internationally accredited third-party auditors. This ensures that qualified timestamps are non-repudiable.
According to the Regulation (EU) No 910/2014 of the European Parliament and of the council on electronic identification and trust services for electronic transactions in the internal market and repealing Directive 1999/93/EC, the term 'Qualified Trust Service Provider' refers to "a trust service provider who provides one or more qualified trust services and is granted the qualified status by the supervisory body".
Qualified timestamps do not contain sensitive data and are therefore not subject to the General Data Protection Regulation (GDPR).
A timestamping service does not require any electronic identity (eID) and does not hold any GDPR-related data.
The object to be timestamped does not leave your infrastructure. You only pass a SHA256 hash of the data object to be timestamped to the timestamping authority (TSA), not the data object itself.
Process overview
Generating a timestamp
To generate a timestamp using Signicat's Qualified Timestamping Authority services, follow these steps:
- Have your data object ready. This can be a file of any type, such as a PDF or an image file.
- Generate a cryptographic hash of the file or text you want to timestamp. The hashing algorithm will need to be SHA256.
- Send this hash to the TSA, which retrieves the correct time from trusted time sources and builds a Signed Data Object (SDO) in the form of a
.tsrfile. - The timestamp has been generated. The SDO can be kept inside the document (this is the case for electronic signatures), but it can also be kept as a separate object.
The following diagram illustrates the generation of a timestamp:
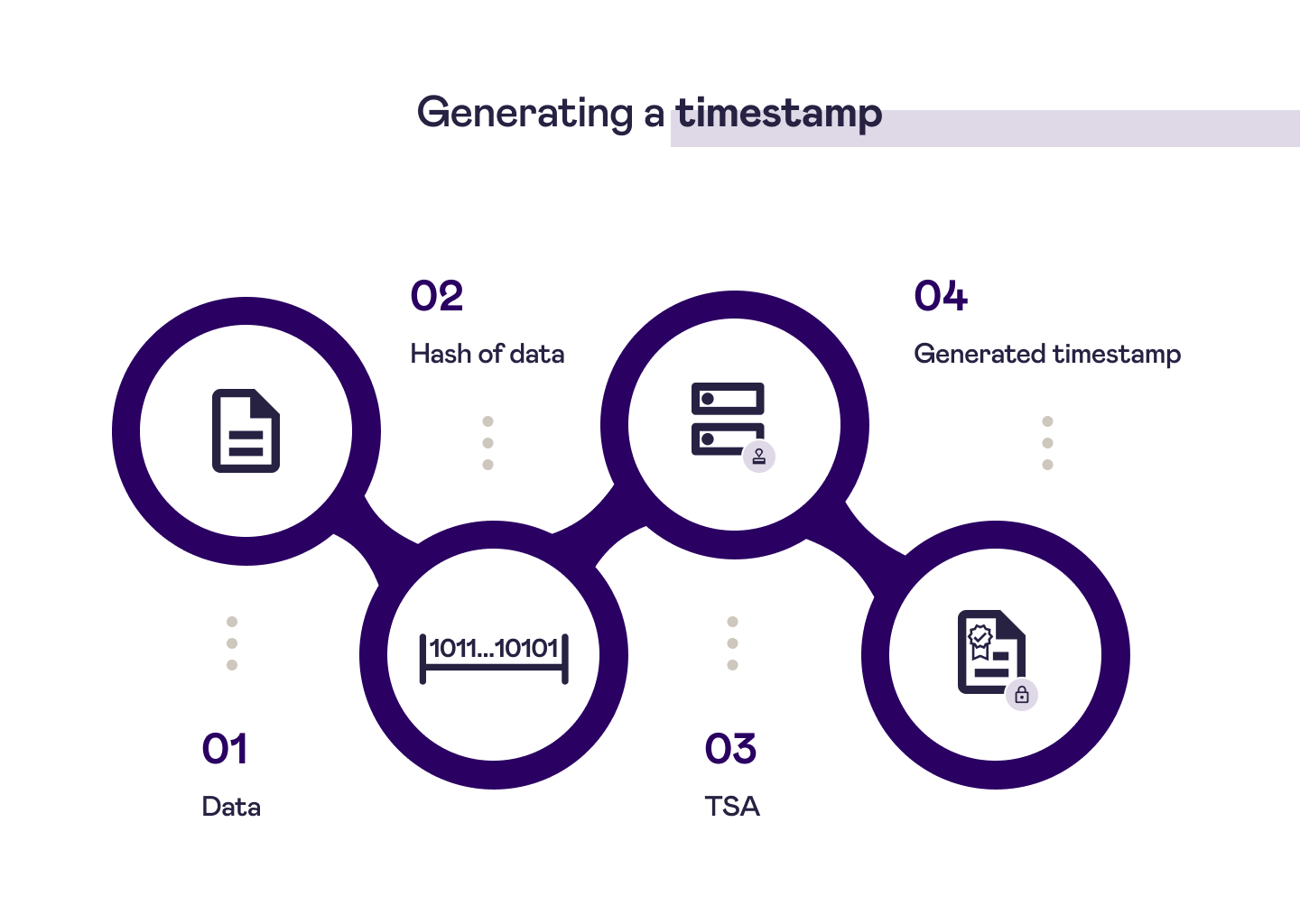
Timestamp generation
Validating a timestamp
To validate a timestamp, follow these steps:
- Have your original data object ready.
- Take another SHA256 hash of the data object. In our example, this is done by
openssl verify. - Provide the timestamp object (SDO) and the public key certificate of the QTSA for verification. The
.pemfile that contains the certificate to be used is available for download in the Validating a timestamp (example) section on this page. - If the document has not been modified, you will receive a positive validation response. Note that the validation does not use the timestamping engine. You can use a service such as
openssl verify.
The following diagram illustrates the validation of a timestamp:
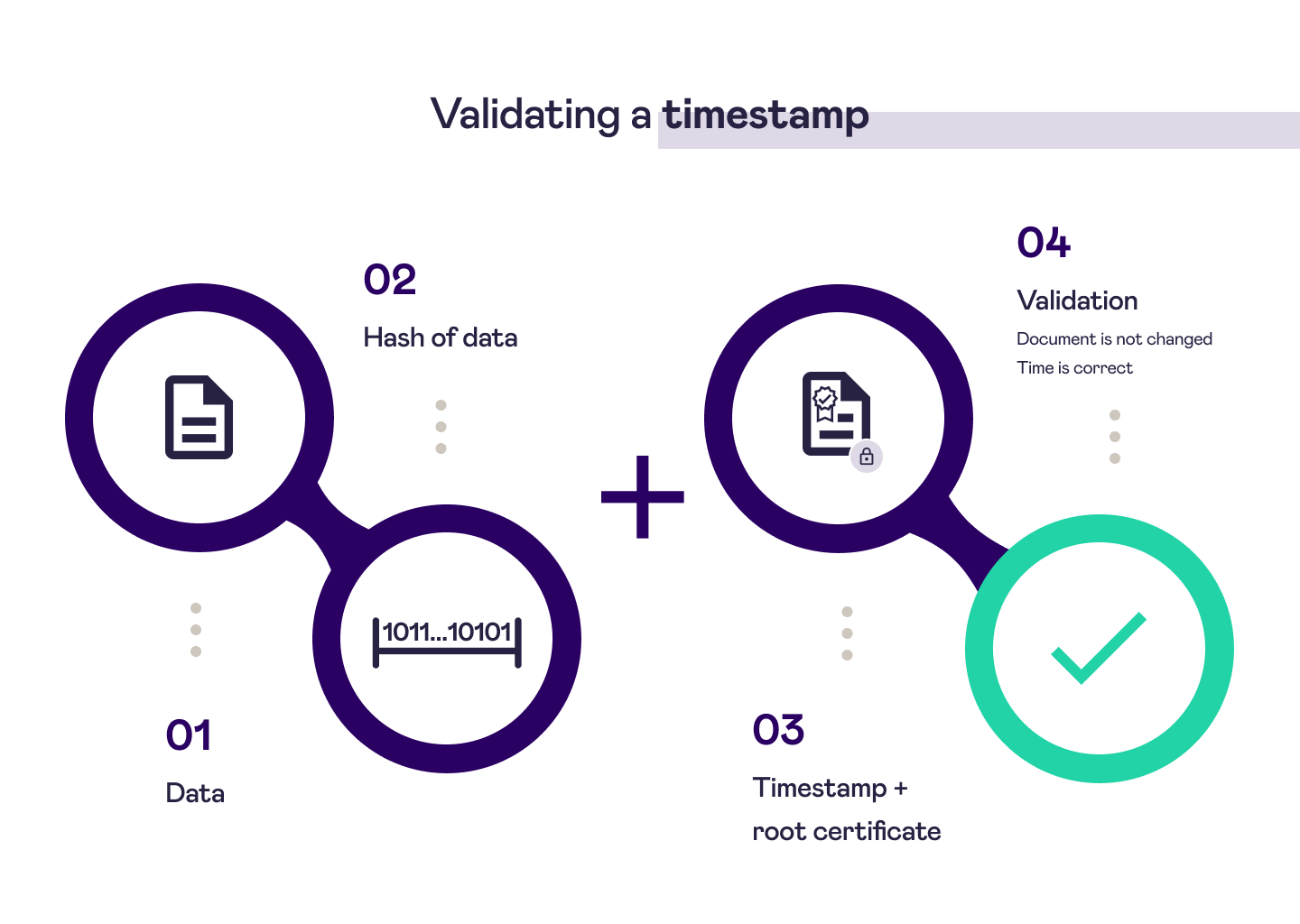
Timestamp validation
Accessing Signicat's QTSA service
To get started with Signicat's QTSA service, contact us at support@signicat.com.
Once you have signed a contract with Signicat and have provided the necessary information, you will be able to access the TSA service at https://tsa.signicat.com/tsaproxy/.
Access to the service works in accordance with the Internet X.509 Public Key Infrastructure Time-Stamp Protocol (RFC3161), which is the common way of accessing any TSA service. Most programming languages have support for RFC3161 through open source libraries.
The interface is the same for both TSA and QTSA. It is common to use a free TSA for testing and then move to the QTSA in production.
Examples of timestamp generation and validation
To run these examples, you will need to have OpenSSL and cURL installed on you computer.
Generating a timestamp (example)
- Generate a timestamp query file (
.tsq) that includes a hash of the data to be timestamped. The example below uses OpenSSL for this operation. - Send the query file to the TSA.
- The TSA produces a signed timestamp response file (
.tsr). Most commonly, this file will be about 1 kB in size and it will be signed and secured in such a way that it cannot be modified.
#!/bin/bash
#Generate request file based on Example.xlsx
echo "Generating .tsq file (query file with hash)"
openssl ts -query -data anyfile -cert -sha256 -no_nonce -out Exampleqtsa.tsq
echo ""
echo "Generating Timestamp into Eaxmpleqtsa.tsr file"
curl -v -s -S -H 'Content-Type: application/timestamp-query' --data-binary @Exampleqtsa.tsq 'https://tsa.signicat.com/tsaproxy/' -o Exampleqtsa.tsr
Validating a timestamp (example)
Validation of a timestamp requires:
- The timestamp object (
.tsrfile) - The public key certificate, contained in a
.pemfile. The public key certificate for Signicat's QTSA is available through the EU Trust Services Dashboard. You can find the.pemfile that contains the certificate here:
The example below uses OpenSSL to verify the public key certificate.
#!/bin/bash
#Generate request file based on Example.xlsx
echo ""
echo "Validate"
openssl ts -verify -data anyfile -in Exampleqtsa.tsr -CAfile signicat_public_key_certificate.pem
echo ""
echo "Dump of timestamp data"
openssl ts -reply -in Exampleqtsa.tsr -text