# OpenID Connect
# Introduction
OpenID Connect (OICD) is a simple identity layer on top of the OAuth 2.0 protocol. It enables clients to verify the identity of the end-user based on the authentication performed by an authorisation server, as well as to obtain basic profile information about the end-user in an interoperable and REST-like manner.
Once you have selected OpenID Connect as the service provider, you will be presented with two configuration choices. You must choose the type of OpenID Connect flow you wish to connect the service provider with.
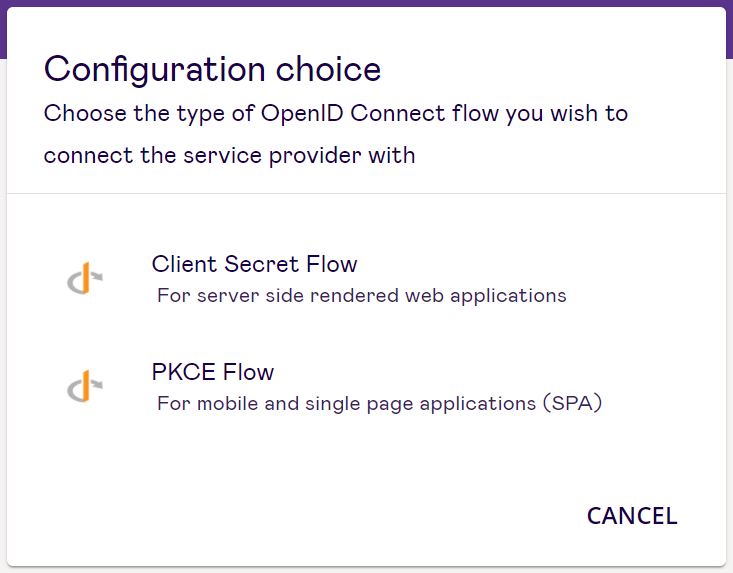
# Configuration
# Client Secret Flow
The Client Secret Flow fields can be configured as follows:
- Name: Name of the connection.
- Use Form Post Response for Authentication Response checkbox: Selecting this returns the response as described in OAuth 2.0 Form Post Response Mode (opens new window).
- Include response from the identity provider checkbox: Selecting this includes an OriginalResponse attribute with the base64 encoded response of the Identity provider.
- Application URL: URL of service provider.
- Client ID: Unique identifier of the client.
- Client secret: A uniquely generated string used for client authentication.
- Redirect URIs: In this section, you can configure multiple redirect URIs.
- Select a LoA contract: Drop-down menu for default and specific LoA contracts. (See Level of Assurance Contracts for more details.)
- Select attribute filter: Select an attribute filter. (See __ Attribute Filters for more information.)
- Select an access token type: There are two options: RANDOM and JWT. If RANDOM is chosen then a random string will be generated as an (opaque) access token. If JWT is chosen then the access token will contain user data and will be signed as well.
- Access token validity: Set a validity duration for the access token in minutes, hours or days. The minimum value is one minute and the maximum value is one day.
- Refresh token validity: Set a validity duration for the refresh token in minutes, hours or days. The minimum value is one minute and the maximum value is 31 days.
- Maximum session validity: Set a validity duration for the session in minutes, hours or days. The minimum value is one minute.
- Backchannel Logout URL: The URL for the IdP initiated logout.
- Response attribute mappings: The user can choose to customise the name of the attributes received in the response body. You can provide none or multiple name-to-name mappings.
# PKCE Flow
The PKCE Flow fields can be configured as follows:
- Name: Name of the connection.
- Use Form Post Response for Authentication Response checkbox: Selecting this returns the response as described in OAuth 2.0 Form Post Response Mode (opens new window).
- Include response from the identity provider checkbox: Selecting this includes an OriginalResponse attribute with the base64 encoded response of the Identity provider.
- Application URL: URL of service provider.
- Client ID: Unique identifier of the client.
- Redirect URIs: In this section you can configure multiple redirect URIs.
- Select a LoA contract: Dropdown menu for default and specific LoA contracts. (See Level of Assurance Contracts for more details.)
- Select attribute filter: Select an attribute filter. (See __ Attribute Filters for more information).
- Select default broker service: Select the default broker service to be used.
- Response attribute mappings: The user can choose to customise the name of the attributes received in the response body. You can provide none or multiple name-to-name mappings.
- Select an access token type: There are two options: RANDOM and JWT. If RANDOM is chosen then a random string will generated as an (opaque) access token. If JWT is chosen then the access token will contain user data and will be signed as well.
- Access token validity: Set a validity duration for the access token in minutes, hours or days. The minimum value is one minute and the maximum value is one day.
- Refresh token validity: Set a validity duration for the refresh token in minutes, hours or days. The minimum value is one minute and the maximum value is 31 days.
- Maximum session validity: Set a validity duration for the session in minutes, hours or days. The minimum value is one minute.
- Backchannel Logout URL: URL for the IdP initiated logout.
- Mobile connection details:
- IOS App ID
- Android App Package Name
- Android App SHA256 Certificate Fingerprint
- App2App redirect URL