# Questions about your connection
# How do I ensure that users are directed (using IdP scoping) to the eIDAS Message Service (the flag screen) from a login button?
It is mandatory to use a separate login button for logging in with eIDAS. If you don't have a separate login button yet, you will have to make changes to your web application for this purpose. All service providers must ensure that a separate login button is placed on their portal.
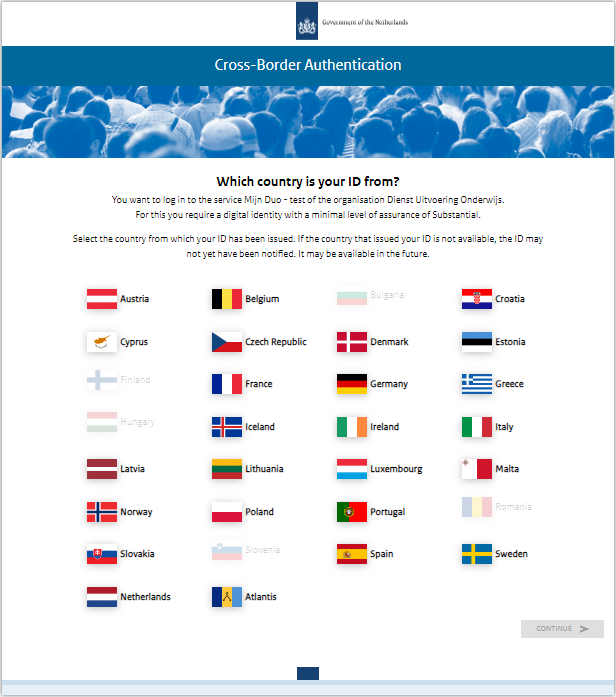
If your organisation is connected to the Signicat Identity Broker and selection of ID methods takes place on your portal or if you are connected to the Signicat eHerkenning Broker, you can use the 'scoping' element to direct the user to the eIDAS Message Service.
This can be done by including the following elements (see from line 16) in the authentication request:
# Broker connections
# Production
<saml2p:AuthnRequest xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"
AssertionConsumerServiceURL="https://customer.website.nl/api/gebruiker-extern/saml/sso/eidas"
AttributeConsumingServiceIndex="1"
Destination="https://signicat.broker.nl/broker/sp/saml/login"
ForceAuthn="true"
ID="_4c2b179988a66bd1881ae933d387c3c1"
IsPassive="false"
IssueInstant="2021-07-23T12:20:04.780Z"
ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Version="2.0">
<saml2:Issuer xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">example_SP</saml2:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">...</ds:Signature>
<saml2p:RequestedAuthnContext Comparison="minimum">
<saml2:AuthnContextClassRef xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">urn:etoegang:core:assurance-class:loa3</saml2:AuthnContextClassRef>
</saml2p:RequestedAuthnContext>
<saml2p:Scoping>
<saml2p:IDPList>
<saml2p:IDPEntry ProviderID="urn:etoegang:EB:00000004000000149000:entities:0001"/>
</saml2p:IDPList>
</saml2p:Scoping>
</saml2p:AuthnRequest>
# Pre-production
<saml2p:AuthnRequest xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"
AssertionConsumerServiceURL="https://customer.website.nl/api/gebruiker-extern/saml/sso/eidas"
AttributeConsumingServiceIndex="9000"
Destination="https://signicat.broker.nl/broker/sp/saml/login"
ForceAuthn="true"
ID="_4c2b179988a66bd1881ae933d387c3c1"
IsPassive="false"
IssueInstant="2021-07-23T12:20:04.780Z"
ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Version="2.0">
<saml2:Issuer xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">example_SP</saml2:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">...</ds:Signature>
<saml2p:RequestedAuthnContext Comparison="minimum">
<saml2:AuthnContextClassRef xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">urn:etoegang:core:assurance-class:loa3</saml2:AuthnContextClassRef>
</saml2p:RequestedAuthnContext>
<saml2p:Scoping>
<saml2p:IDPList>
<saml2p:IDPEntry ProviderID="urn:etoegang:EB:00000004000000149000:entities:9008"/>
</saml2p:IDPList>
</saml2p:Scoping>
</saml2p:AuthnRequest>
# Direct connections
# Production
<saml2p:AuthnRequest xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"
AssertionConsumerServiceURL="https://customer.website.nl/api/gebruiker-extern/saml/sso/eidas"
AttributeConsumingServiceIndex="1"
Destination="https://eh.signicat.nl/broker/sp/eh/1.13/login"
ForceAuthn="true"
ID="_4c2b179988a66bd1881ae933d387c3c1"
IsPassive="false"
IssueInstant="2021-07-23T12:20:04.780Z"
Version="2.0">
<saml2:Issuer xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">example_SP</saml2:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">...</ds:Signature>
<saml2p:RequestedAuthnContext Comparison="minimum">
<saml2:AuthnContextClassRef xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">urn:etoegang:core:assurance-class:loa3</saml2:AuthnContextClassRef>
</saml2p:RequestedAuthnContext>
<saml2p:Scoping>
<saml2p:IDPList>
<saml2p:IDPEntry ProviderID="eherkenning"/>
<saml2p:IDPEntry ProviderID="urn:etoegang:EB:00000004000000149000:entities:0001"/>
</saml2p:IDPList>
</saml2p:Scoping>
</saml2p:AuthnRequest>
# Pre-production
<saml2p:AuthnRequest xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"
AssertionConsumerServiceURL="https://customer.website.nl/api/gebruiker-extern/saml/sso/eidas"
AttributeConsumingServiceIndex="9000"
Destination="https://eh.pre.signicat.nl/broker/sp/eh/1.13/login"
ForceAuthn="true"
ID="_4c2b179988a66bd1881ae933d387c3c1"
IsPassive="false"
IssueInstant="2021-07-23T12:20:04.780Z"
Version="2.0">
<saml2:Issuer xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">example_SP</saml2:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">...</ds:Signature>
<saml2p:RequestedAuthnContext Comparison="minimum">
<saml2:AuthnContextClassRef xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">urn:etoegang:core:assurance-class:loa3</saml2:AuthnContextClassRef>
</saml2p:RequestedAuthnContext>
<saml2p:Scoping>
<saml2p:IDPList>
<saml2p:IDPEntry ProviderID="eherkenning"/>
<saml2p:IDPEntry ProviderID="urn:etoegang:EB:00000004000000149000:entities:9008"/>
</saml2p:IDPList>
</saml2p:Scoping>
</saml2p:AuthnRequest>
TIP
For more information, see the Afsprakenstelsel interface specifications (opens new window).
# How do I test my connection on pre-production?
During testing, select the "pre-production" option from your respective token provider (see example image).
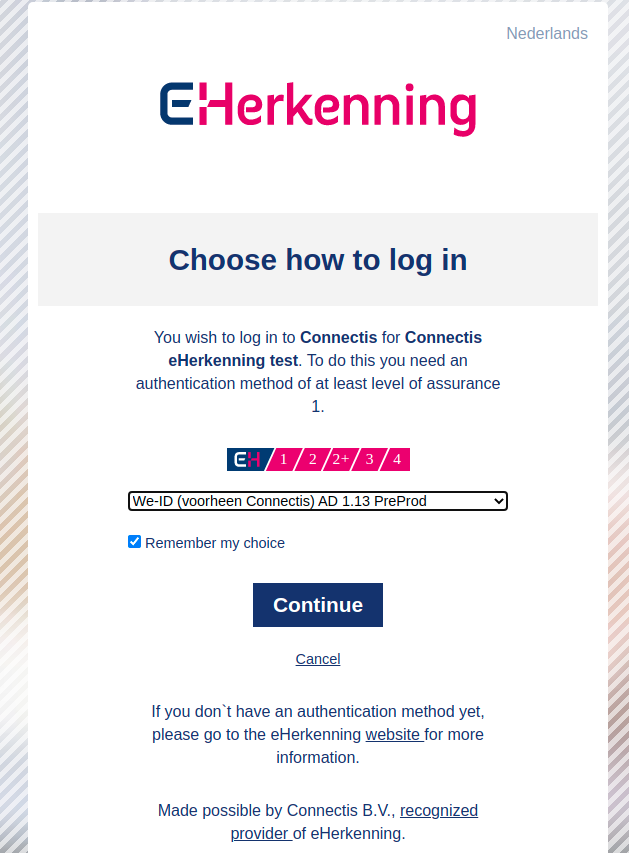
# How can I test my eIDAS pre-production connection?
When not directly scoping to the eIDAS Message Service, choose the "Dictu EB (Acceptance)" option.
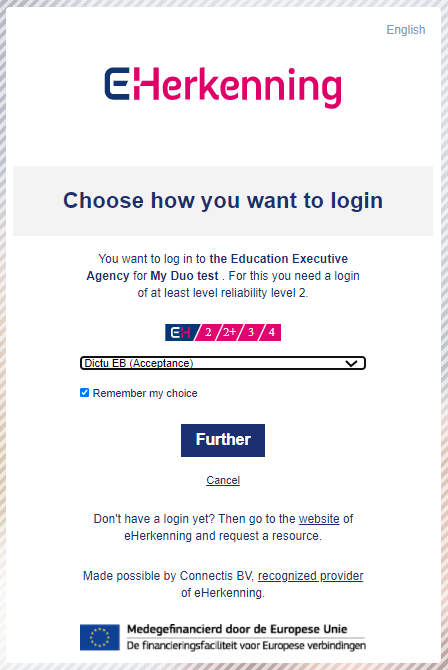
Choose to log in for the fictional country Atlantis (the last option).
Use the following publicly available test tokens:
test_user_bsn_loa3test_user_bsn_loa4test_user_pseudoid_loa3test_user_pseudoid_loa4
Please contact Support if you need a test token with different attributes assigned to it.
# How can I test my eIDAS production connection?
Obtaining your own production eIDAS token is quite cumbersome. You would need to contact the Foreign Affairs Department of your nation state to provide you with a token.
Please contact Support and ask them to test the connection for you, as the team is already in the possession of production test tokens.
# How can I purchase a test token?
You can apply for a test token by using the following link: Application for eHerkenning test token (opens new window) (in Dutch).
In the application form you can indicate which attributes the test token should have.
# Can I connect several service providers to one connection?
No. A connection is linked to the Organisational Identification Number (OIN) of the service provider. It is not possible to link several OINs to one connection.
# Do I need a new connection for every service?
No, you can use multiple services via the same connection. A one-to-one or a one-to-many relationship can be established between a connection and service(s).
# What certificates can I use for an eHerkenning connection?
For eHerkenning, you need to deliver PKIoverheid certificates for both our pre-production and production environments. This is a requirement from the Afsprakenstelsel (opens new window).
# What should I be aware of when applying for PKIoverheid certificates?
Please note the following when applying:
- The OIN of your organisation is included in the Serial field of your certificate. This may need to be stated explicitly.
- The type of PKIoverheid certificate is "Private Services CA G1" or "Private Services CA - 2023".
- The certificate has been purchased from one of the recognised suppliers.
- The bit strength of the certificate should be 4048.
# How can I get an OIN if I do not have one to hand?
Most organisations already have an Organisational Identification Number (OIN). If you have not yet applied for one, you can do so via this link (opens new window) (in Dutch).
If your organisation is not eligible for an OIN, please contact Technical Support (see below). An OIN will be drawn up on the basis of the Chamber of Commerce (KvK) number instead.
# In which programming languages do you offer adapters/SDKs?
Our adapters are available in Java and .NET. More information about the Signicat Adapters here.
# Does the Signicat adapter support multi-tenant or do I need to set up an adapter for each tenant on my service?
It is not necessary to install an adapter per tenant. The Signicat adapter supports multi-tenant.
# Why can I not use HTTP connections (to localhost) to test the Identity Broker integration?
Because HTTP connections are not considered secure, they are not allowed to be configured. All connections must go over HTTPS. HTTP connections are considered to be non-conformities in different audits, even if they are to localhost applications on testing environments.
Since security is important in authentication flows, we do not make exceptions on allowing HTTP connections.
To make use of HTTPS on localhost environments, we suggest having:
- a DNS entry for your company domain that points to 127.0.0.1 (we have *.local.test-development.nl for example )
- a cheap certificate for this DNS entry that is shared with all relevant developers.
Does your question remain unanswered? You can reach our Technical Support department Monday to Friday from 09:00 to 17:30 via email at technicalsupport@signicat.com or by calling + 31 (0)88 012 0210.