# Direct Connection to eHerkenning Broker
IMPORTANT
This chapter discusses direct connections to the eHerkenning Broker. If you are using the Signicat Identity Broker, instead follow the steps for integration of eHerkenning in the Identity Broker.
# Signicat eHerkenning Broker metadata and TLS certificate
# TLS
Your application may need to trust the Signicat eHerkenning broker TLS certificates.
The names of the certificates are:
- eh.pre.signicat.nl.crt (preprod)
- eh.signicat.nl.crt (prod)
The certificates for both pre-production and production are issued by "Sectigo RSA Domain Validation Secure Server CA".
You can download them here directly:
- Pre-production: Download certificate
- Production: Download certificate
# Metadata
Your application may need to use the Signicat eHerkenning broker signing certificates. These are part of the broker metadata and are used for signing of our messages.
We have eHerkenning metadata available for the version you are using in your service application: 1.11 or 1.13. You can download them here directly:
# eHerkenning 1.11
Pre-production:
Keyname for new certificate as of 2024-08-24:
4dc9da80de223da7d0d7dc63a5f80a93216ab73200f6797e85080422657bb5d8
Production:
Keyname for new certificate as of 2024-08-27:
fd3cc0d7ae7dd96ed34c9fcef74a71817657219aa1dd0c71e065eb3fd32b07ae
# eHerkenning 1.13
Pre-production:
Keyname for new certificate as of 2024-08-24:
4dc9da80de223da7d0d7dc63a5f80a93216ab73200f6797e85080422657bb5d8
Production:
Keyname for new certificate as of 2024-08-27 :
fd3cc0d7ae7dd96ed34c9fcef74a71817657219aa1dd0c71e065eb3fd32b07ae
For Existing Customers: Please change certificates before August 2024
Existing customers using the eHerkening broker must change their metadata and TLS certificates.
For dates and details, see Upcoming changes > Change signing certificate for eh.signicat.nl (August 2024)
# Login representation flow
The representation flow is the flow where the user logs in to act on behalf of a company.
Step 1: The service provider sends an AuthnRequest to the eHerkenning broker via Artifact binding, Post binding or Redirect binding to the relevant SingleSignOnService of the eHerkenning broker from the metadata.
Example:
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact"
Location="https://eh01.staging.connectis.nl/broker/sso/1.13"/>
Example AuthnRequest:
<saml2p:AuthnRequest xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol"
AttributeConsumingServiceIndex="6"
Destination="https://eh01.staging.connectis.nl/broker/sso/1.13"
ForceAuthn="false"
ID="_91b639b6cdeb6fe2c618f762a9b96e9a"
IssueInstant="2021-04-23T11:28:42.471Z"
ProviderName="Example"
Version="2.0"
>
<saml2:Issuer xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">urn:etoegang:DV:00000003244440010000:entities:0006</saml2:Issuer>
</saml2p:AuthnRequest>
Step 2: The eHerkenning Broker verifies the signature and SAMLRequest.
Step 3: The eHerkenning Broker determines the service that is being requested, based on the OIN of the issuer and the AttributeConsumingServiceIndex.
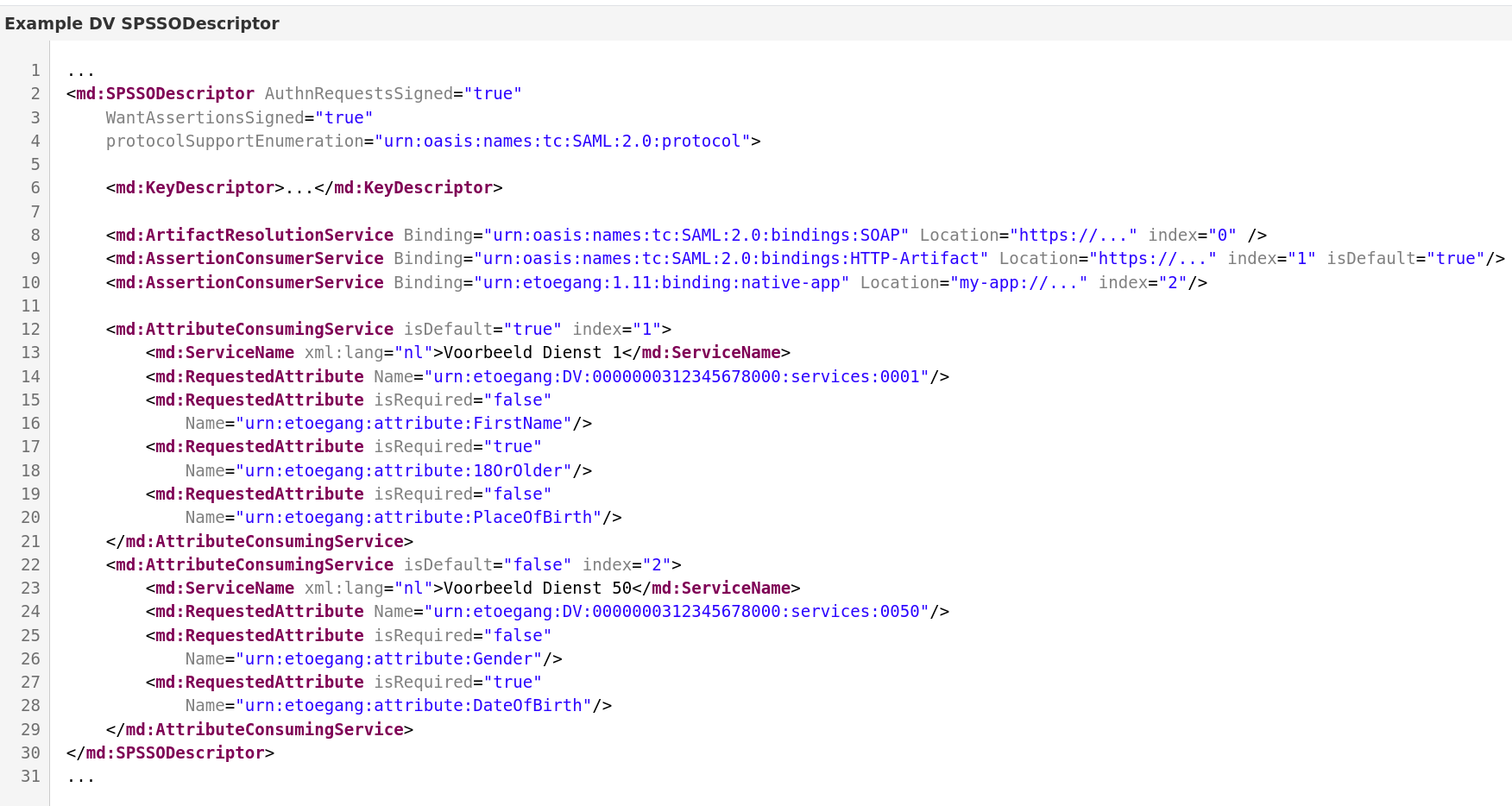
The AttributeConsumingServiceIndex could optionally be mapped by AttributeConsumingServices in the metadata to another index. In below example, index 2 maps to index 50. And, if no AttributeConsumingServiceIndex is sent, index will be 1 (because of isDefault)
Step 4: Show IdP selection screen. Filter IdP from the network metadata based on:
- requested LoA (each IdP specifies a maximum LoA they support)
- Requested ECTAset (some IdPs do not support certain ECTA, e.g. Pseudo)
Step 5: Create an IdP request and send to the IdPs Single SignOn Service using Artifact binding.
Example: https://acc-ehlogin.we-id.nl/ad113_preprod/process?SAMLart
Once the above steps have been followed, next, you access eHerkenning.
# Access the eHerkenning Broker
To proceed, an authentication method with at least a Level of Assurance (LoA) 3 must be used. More information on purchasing an eHerkenning Level 3 supplier can be found on the leveranciersoverzicht (opens new window) page.
Using the dropdown, select the provider of the authentication method to choose how to log in.
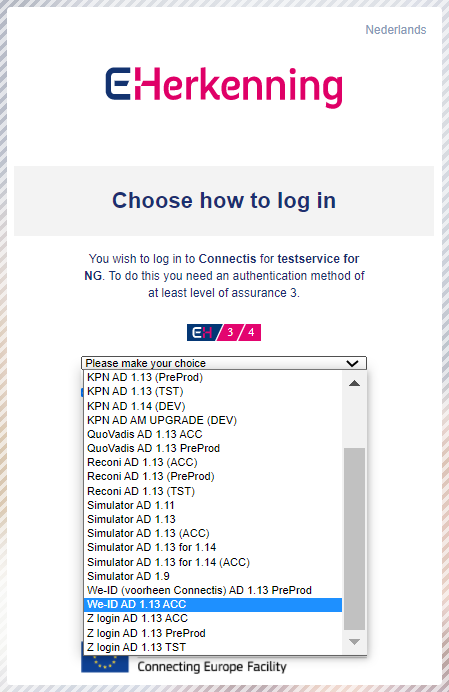
# eHerkenning Level 3 suppliers
You can choose an authentication method from the following suppliers that offer LoA level 3. Use the links to find out more about each supplier:




