# About MitID
MitID (opens new window) is a new electronic ID in Denmark, replacing NemID. It is a collaboration between the Danish banks and the Danish public sector. This alliance forms a nationwide solution and provides a secure authentication mechanism for all Danish citizens and residents. MitID can be used for online banking, Digital Post, communication with public authorities, identifying yourself in other digital services and more.
# Key features of MitID
This is an overview of important features in MitID:
- A common, national identity and authentication solution.
- Public actors, financial institutions and other private service providers can only use MitID through certified brokers.
- Secure login supporting all three levels of assurance (LoA) from eIDAS, Low, Substantial and High:
- Low: Authenticates the user with single-factor authentication, e.g. with password or chip.
- Substantial: Authenticates the user with a two-factor authenticator combination, e.g. with the MitID app on a smart phone.
- High: Authenticates the user with a more advanced two-factor authenticator combination, e.g. the MitID app + chip.
# Level of assurance and authenticators
This section gives an introduction to MitID assurance levels, MitID authenticators and how the combination of different authenticators fulfils different assurance levels.
# NSIS
MitID is regulated according to the Danish NSIS (opens new window) standard, which is the Danish version of eIDAS (opens new window) (Electronic Identification and Trust Services in EU). This means that you as a service provider must follow the NSIS standard and do a risk assessment of the information you give access to with MitID. There is a guide (opens new window) in the NSIS material that may help you as a service provider choosing the right assurance level (LoA).
# Level of Assurance (LoA)
LoA for a MitID transaction has three possible values: Low, Substantial or High. LoA is calculated based on three assurance level components:
- IAL (Identity Assurance Level) represents the strength of the user’s MitID registration. It can only be increased through additional registration processes.
- AAL (Authentication Assurance Level) is calculated based on the authenticators used during an authentication.
- FAL (Federation Assurance Level). MitID implements the NSIS requirements for FAL at level High, so this attribute will always have the value “High”.
The resulting LoA of a transaction is determined by the lowest value present among these three components. Since FAL is always “High”, the LoA is in practice determined by the AAL and IAL. When requesting an authentication, the request can either specify a target LoA or a target AAL.
See also descriptions of these levels in the MitID user information section.
# Authenticators
With MitID, the end-user logs in with a username in combination with one or two authenticators.
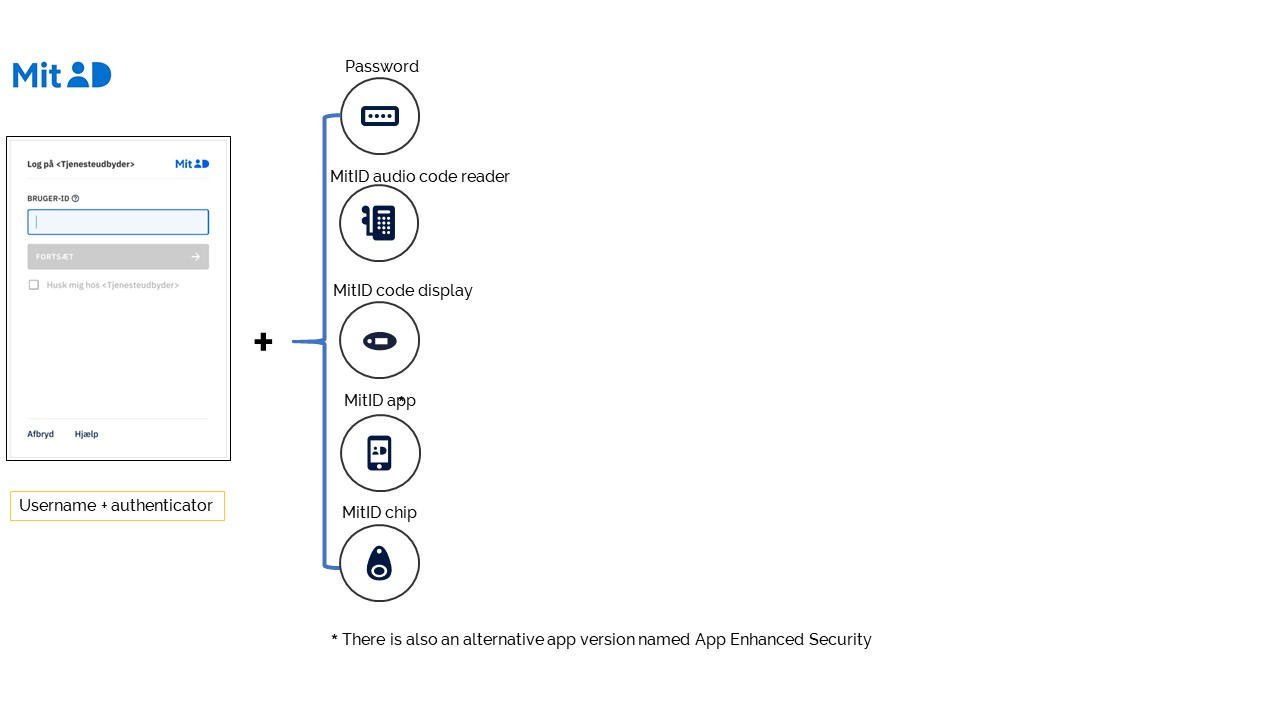
The username decides the possible authenticators, i.e. MitID knows which authenticators a user has registered and can choose between during authentication.
MitID offers the use of the following authenticators:
- MitID app: The user can use this app when a secure element is present in the hardware or in combination with the MitID chip, assuming proper activation. Both will give a High LoA. There is an alternative version of this app named App Enhanced Security. With this app, the user must enrol on a device with SE/TEE technology (secure element/trusted execution environment). These technologies are possible elements included in the NFC technology (Near Field Communication for smartphones). The user should not enable biometric unlocking of the app. This prevents the use of multi-user functionality.
- MitID code display: A physical device authenticator showing a one-time password (OTP) to be typed into the service provider’s user interface within a certain time. It is based on OATH TOTP (RFC 6238 (opens new window)).
- MitID audio code reader: A sound-based TOTP (opens new window) token (time-based one-time password algorithm). The device reads aloud the OTP code to the user so the user can enter it in the service provider’s user interface. This is an alternative for visually impaired or if the user does not want to use the code app.
- MitID chip: This is a chip that supports the FIDO U2F standard. The end-user can combine this with the password or the app for reaching High LoA.
- Password: A password authenticator implementation based on the Secure Remote Password (SRP) (opens new window) protocol.
When an end-user has migrated to MitID, they can choose one of two authenticator combinations to start off:
- MitID app.
- Password + MitID code display or code reader.
Both these combinations are sufficient to reach AAL substantial. The MitID chip authenticator is not available immediately upon migration, but can be ordered by the user on mitid.dk (opens new window).
# Possible authenticator combinations
MitID supports different combinations of authenticators. Single-factor authentication can be to combine a username with one of the mentioned authenticators, for example a password. If higher security is needed, you can use a more secure authenticator, such as MitID app or use two-factor authentication, e.g. combining a password with MitID code display.
The following table (from the MitID broker package documentation) shows possible combinations of authenticators and what level of assurance the combinations give (Low, Substantial and High):
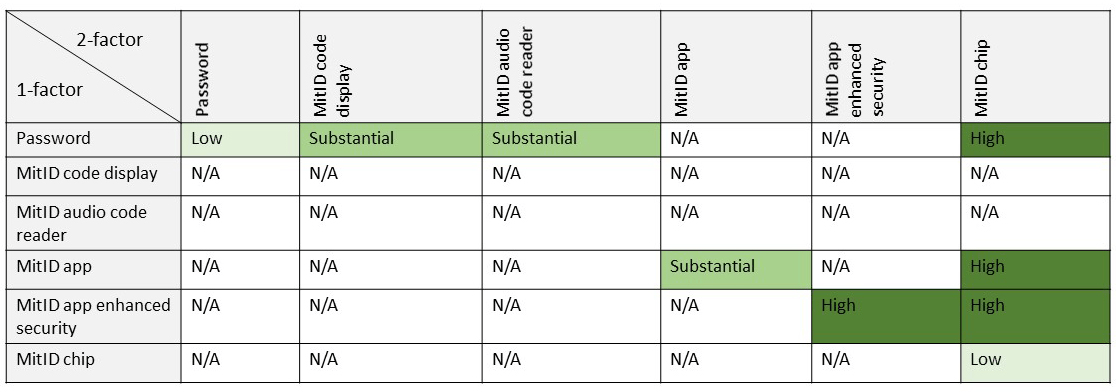
For example, password together with a MitID code token gives two-factor authentication with Substantial AAL. Password together with the MitID chip gives two-factor authentication with High AAL etc.
Note: As a broker, Signicat supports all MitID authenticators. MitID decides the possible combinations.
# Low
With Low AAL, you can allow your users a simple login with password or chip.
# Substantial
Substantial achieves the equivalent AAL of NemID authentications.
# High
With High AAL, you can achieve the highest level of confidence using a two-factor authentication of your users.
# Other sources
- Information to the public about MitID on the Digitaliseringsstyrelsen website (opens new window) (in Danish).
- Signicat external web site (opens new window).