# Authenticator App
Page contents
# About the Authenticator App
The Authenticator App is a white-label mobile application that serves as the mobile GUI for activation, authentication and authorisation processes. It uses the Encap Client SDK for communication with the Encap server and is protected against malware and tampering by Promon SHIELD™.
Note
You can use this Authenticator App if you are a customer of MobileID or hosting Encap SCA on-premises.
# How does the Authenticator App work?
The Authenticator App implements two key process flows:
- Activation
- Authentication and authorisation
# Activation
Before you can start using the Authenticator App, you need to first activate the device and create authentication credentials.
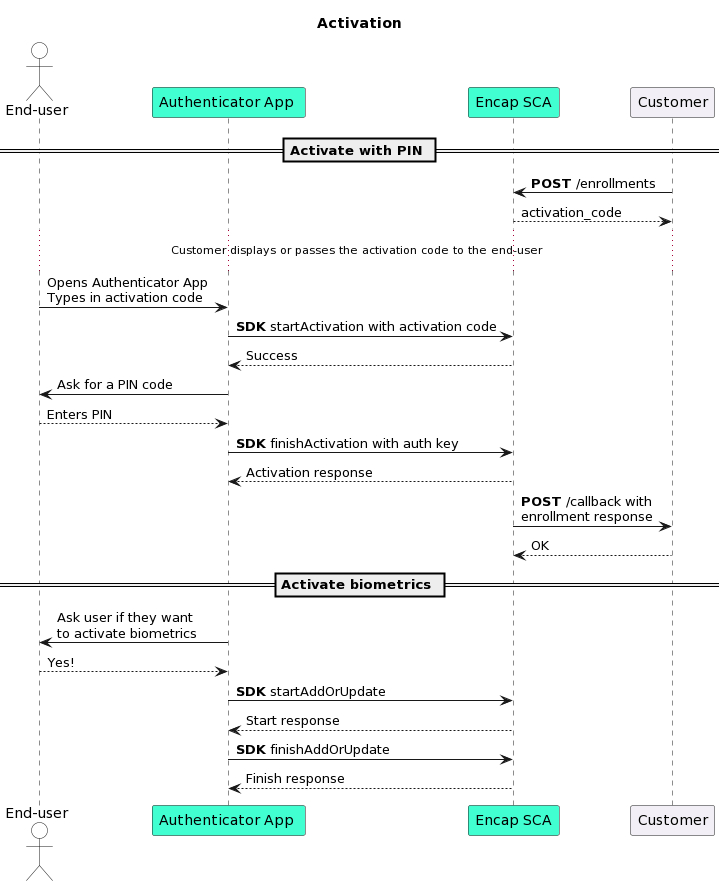
# Activation code
The application is activated with an activation code. The activation code is generated by Encap SCA and passed to you after an activation has been initiated. It is your responsibility to display the activation code to the user in the preferred channel; for example, this could be a web page after the user has authenticated themselves.
The app has built-in support for scanning QR codes during enrolment.
- This provides a better user experience for the end-user, as they can scan the code instead of entering it manually.
- This makes it easier to use longer and more secure activation codes.
To use this, you must generate a QR code and display it to the end-user. The end-user can then scan the QR code with the camera on the device.
Note
The button for scanning QR codes is located next to the field for manual activation code entry.
# Activate authentication methods
Once the activation code has been successfully verified, the end-user must then select a PIN. If biometrics are supported in the application configuration, then the end-user also has the option to activate a biometric authentication method.
Note
The device (as an authentication method) is always activated in the background when activating a PIN, therefore enabling you to perform both one-factor and two-factor authentication.
# Authentication and authorisation
Once the Authenticator App has been activated, it can be used to perform authentications and authorisations with one-factor or two-factor authentication.
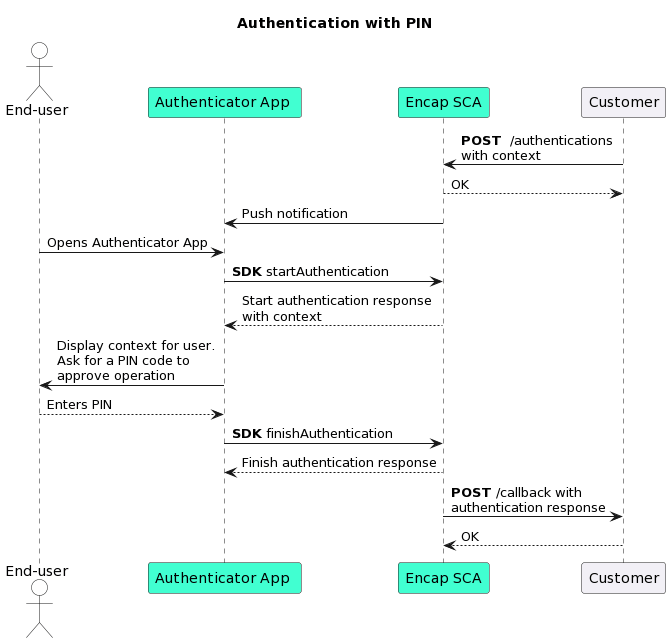
When you want to authenticate an end-user, you must initiate an authentication with Encap SCA. An optional push message can be sent to the device to notify the end-user, if this is configured in the application configuration.
The Authenticator App supports both a PIN code and biometrics as the second factor. If biometrics have been activated on the device, then the app will default to this method and use the PIN code as the fallback.
Note
You can specify what authentication method the end-user should use when initiating the authentication.
You can also choose to authenticate the user with only one factor using the device (as an authentication method). In this implementation, the Authenticator App will only show the Approve and Decline buttons to the end-user.
# Operation context
For each operation, you can set a context, which is a text that is passed to the mobile device. This allows you to send important information to the end-user, through a secure channel with end-to-end encryption (E2EE).
This information can be passed:
- Before the operation has been approved (pre-operation context).
- After the operation has been successfully completed (post-operation context).
# Example use cases
- Ask the end-user for approval of an operation, such as when the operation is initiated in a different channel to your application.
- Conduct PSD2 RTS-compliant payment transactions.
- Share secret information with the end-user that you only want to be available on the device after a successful operation (such as a PIN code).
Want to learn more?
For more information on operation context, see our MobileID feature documentation. Note that the linked documentation describes MobileID's implementation of operation context. If you are not a MobileID customer, then some of the documentation will not be applicable to you.
# Authentication methods
On the Encap Server, you must decide which authentication methods to make available to the end-user. The options are:
- Device
- PIN code
- Biometrics (Face ID, Touch ID, BiometricPrompt, Fingerprint)
# Additional features
The following features are available in the Authenticator App once it has been activated:
Activate/deactivate supported biometric authentication methods
The end-user has the option to activate/deactivate biometric authentication methods, on devices that support this.
Change PIN
The end-user has the option to change the PIN code.
Deactivate
The end-user has the option to deactivate the registration and delete the activation data from the device. If an error occurs during deactivation against the Encap server, then an option to wipe the registration locally on the device is presented to the end-user.
Passport scan
You can use this feature to gather passport attributes, process the passport data, and verify the passport's authenticity.
You can collect properties such as:
- The portrait picture in the passport.
- The picture that was taken of the data page during the scan.
- A JSON file containing information about the contents that can be retrieved from Electronic Machine Readable Travel Documents (eMRTD), in addition to information about the verification process.
For more information on passport scanning, see our MobileID feature documentation. Note that this feature is only available for MobileID customers.
Runtime Application Self Protection (RASP)
Promon SHIELD™ is a security technology that integrates directly into applications to provide proactive security against a wide range of attacks, such as tampering, debugging, code injection, code modification and stealing of data from the app.
If Promon SHIELD™ detects that the device is jailbroken, it will alert the end-user:
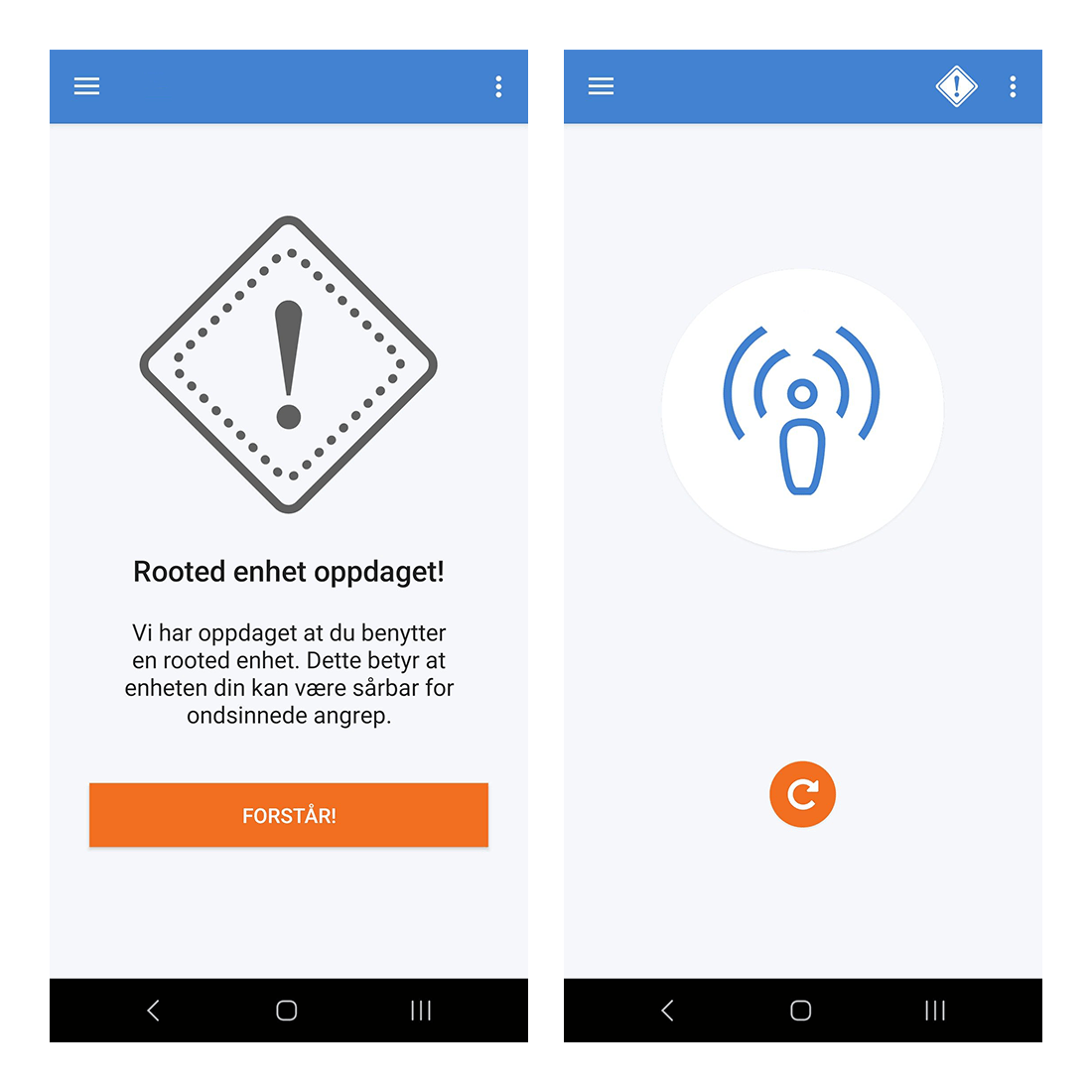
The information will also be sent to the Encap Server as a risk parameter.
# Configuration options
The Authenticator App can be configured in the following ways:
# Mobile application configuration
The following are required to configure the application:
| Configuration | Description |
| Server URL |
The relevant Encap SCA server URL needs to be set.
|
| Application ID | The application ID is required. This is the identifier for the application configuration. |
| End-to-end (E2E) keys |
Encap SCA uses end-to-end encryption between smart device clients and the server. If you are hosting your own Encap server, then you need to:
|
# Encap SCA application configuration
This configuration is stored server-side, and contains details for how the specific app should behave.
For example, you can specify which authentication method to support, configure security features like app attestation and geofencing, set up push notifications and much more.
You can read more about what can be configured at the following links:
- For Encap SCA customers, see section 4.2.2 The configuration object (opens new window) in our Encap SCA API Guide.
- For MobileID customers, see Application configuration (opens new window) in our MobileID developer documentation.
# Push notifications
The Authenticator App supports push notifications. Push notifications are an optional feature, and are only used to notify the end-user that an operation has been initiated.
To enable push notifications, it needs to be configured in the application configuration on the server.
Note
If you are using our MobileID service, we will configure the application configuration for you. However, you still need to create the APNS token/certificate and configure Firebase Cloud Messaging.
See Application configuration (opens new window) for further details.
# Apple Push Notification Service (APNs)
You can read more about getting started with APNs in our Mobile Identity Partner Wiki (opens new window).
- See section 4.12 Push Notifications in our Getting started with Encap Client API for iOS document.
- See our Apple APNs certificate/token creation document under Server setup and Service provider integration.
# Firebase Cloud Messaging (FCM)
You can read more about getting started with FCM in our Mobile Identity Partner Wiki (opens new window).
- See section 4.8. Firebase Cloud Messaging (FCM) push in our Getting started with Encap Client API for Android document.
# Promon SHIELD™
Promon SHIELD™ is required when using our Authenticator App. The security mechanisms from Promon SHIELD™ can be configured to behave according to the desired security policy. We can shield the app for you, or you can choose to shield the app yourself.
If we are to shield the app for you, you must provide the application signing key (applicationSignerTeamID/applicationSignerCertificate).
Note
We can also make changes to the default configurations if required.
# Localisation
The Authenticator App supports English, Norwegian, Swedish and Finnish. If you wish to add another language, please reach out to us at support@signicat.com for further details.
# Branding
You can customise the appearance of the Authenticator App with your own branding, by supplying the following resources:
- The name of the app.
- The application icon.
- The logo on the welcome page and home page.
- The colour value for various elements within the app, such as the toolbar, button colour and background colour.
- The launch image or splash screen, which is displayed during the launch of the app.
- The notification icon.
- The help page.
See our Authenticator App branding guide for further details:
# Supported operating systems
The Authenticator App supports the following operating systems:
- Android 9.0 and later.
- iOS 15.0 and later.
# Deployment
We deliver the Authenticator App app to you as an APK or XCARCHIVE file. It is your responsibility to sign and publish the app on the App Store and Google Play.
This will require a developer account for the relevant platforms. If you do not have an account, you will need to sign up for one.
Note
We can assist you with more detailed instructions and support if necessary.
# Demo
You can see what the Authenticator App looks like and how it can be used in our YouTube videos (opens new window). These videos demonstrate the Authenticator App being used in our demo bank (West Springfield Bank).
# Try it out
If you want to try it out, you can contact us at support@signicat.com. We will provide you with access to the mobile app and the demo environment.